How we help service providers
HOW WE HELP SERVICE PROVIDERS
Easy-to-manage innovative solutions and exclusive resources for growing MSPs
POWER OF THREE
Our MSP-dedicated business unit combines the experience and expertise of three service provider software suppliers (QBS, Zedsphere and 4Serv).
We care about our service provider community – getting to know them as people, understanding their business needs, and introducing them to products that will position them as industry leaders, add to their monthly recurring revenue, and ensure their customers are satisfied.
We care about our service provider community – getting to know them as people, understanding their business needs, and introducing them to products that will position them as industry leaders, add to their monthly recurring revenue, and ensure their customers are satisfied.
CHAMPIONS OF XAAS
In the constantly evolving IT services industry, we find the tools IT providers need to keep them at the leading edge.
With a rigorous selection process – including technical, cultural, commercial and political position elements, we iron out any complex issues at the outset.
Ultimately, guided by our community in the selection of our final portfolio, we know our offering not only has our stamp of approval, but the industry’s too.
With a rigorous selection process – including technical, cultural, commercial and political position elements, we iron out any complex issues at the outset.
Ultimately, guided by our community in the selection of our final portfolio, we know our offering not only has our stamp of approval, but the industry’s too.

Cloud Hosted
Multi Tiered

Multi Tenanted

Monthly Billed

MSP Friendly
CUSTOMER SUCCESS DAY IN DAY OUT
We ensure customer success by providing educational and informative advice on how our partners can improve their business and find the right tools to help them and their customers grow.
We also provide a valuable online resource library, regular webinars and bespoke vendor programmes introducing new products to partners exploring new or alternative solutions.
We also provide a valuable online resource library, regular webinars and bespoke vendor programmes introducing new products to partners exploring new or alternative solutions.
EFFICIENT OPERATIONS & SERVICE
Once we know a partner’s solution requirement, our technically-trained specialists work with them to ensure the optimum fit. We work closely with our vendors to deliver the smooth, snag-free service our partners enjoy.
We provide full licensing and fulfilment details as well as a technical on-boarding experience. This may include a pre-sale demonstration as well as assistance in the set-up and configuration of a free trial account. If required, we can also assist with post-sale configuration and 1st line technical support.
We provide full licensing and fulfilment details as well as a technical on-boarding experience. This may include a pre-sale demonstration as well as assistance in the set-up and configuration of a free trial account. If required, we can also assist with post-sale configuration and 1st line technical support.
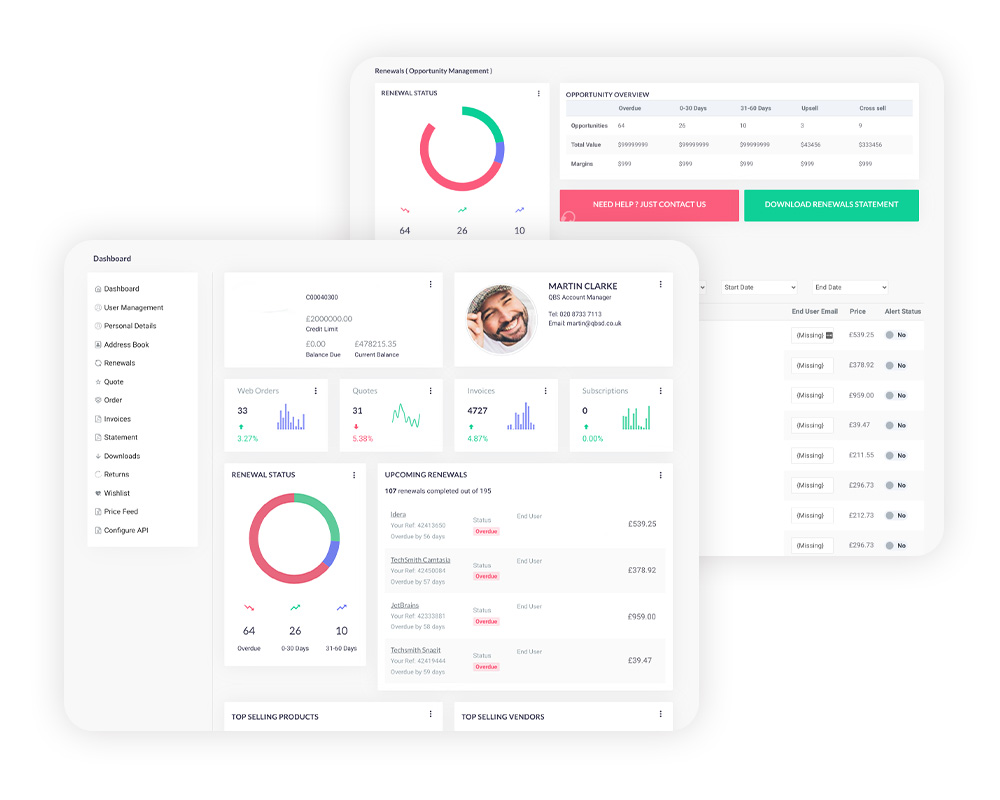
ONLINE ACCOUNT MANAGEMENT & MONTHLY BILLING
We currently manage billing and licensing for 400+ end users and provide single monthly invoices for our partners, including monthly direct debit options.
As well as having a dedicated account manager, partners can generate self-service quotes via our customer portal, and benefit from user/usage reporting and renewals management.
As well as having a dedicated account manager, partners can generate self-service quotes via our customer portal, and benefit from user/usage reporting and renewals management.